Any trader working on the Ethereum blockchain has experienced mental anguish due to the negative impact MEV has had on their ability to complete trades. A recent study indicates that there were an estimated 1,999 sandwich attacks daily generating an average loss of $2 million/ month per trader via trades concluded on decentralized exchanges if executed within the last month.
Most transactions for swap trades using various types of wrapped assets, including both wrapped BTC and stable coins, will also suffer substantial losses as a result of front-running or back-running strategies executed through automated MEV bots. Often these transactions are executed at scale on a few million dollars' worth of swap trades.
How MEV Exploits Blockchain Transparency
Public mempools create predictable targets
Because all blockchain (on chain) transactions are viewable before they have been confirmed, there is an opportunity for profit-making through the use of MEV (maximum extractable value). When a trader initiates a transaction, it will initially be placed in the mempool. At this point, both validators and bots are able to use the following information about the trader's intended transaction to see if they can insert or vary the order of their own transactions to take advantage of the price movements resulting from that original transaction:
.token-pair
.size of trade
.slippage tolerance
.gas priority
This public visibility of transactions that is essential to the decentralization of blockchains also allows for adversarial activities by some parties.
Real World Impact of Sandwich Attacks
Bot purchases an asset prior to the time of execution of the victim's swap
Victim executes the transaction at a lower price than was executed by the bot when they purchased the asset.
Bot then sells the asset for a profit immediately after executing the victim's transaction.
Micro losses from thousands of transactions daily accumulate into total losses of millions of dollars each month for traders.
Visualizing Sandwich Attack Flow
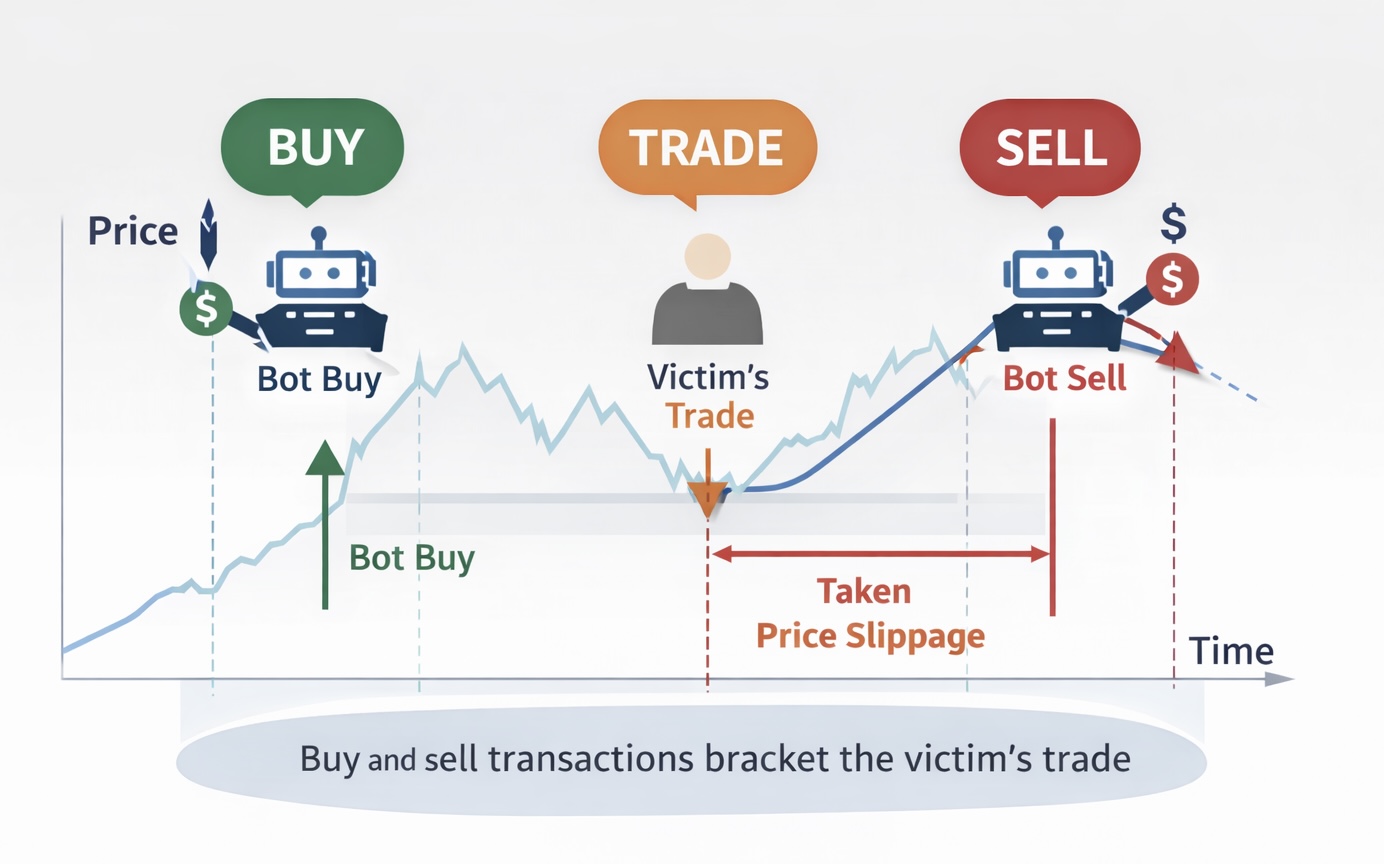
Image Source: Author
Encrypted Mempools as a Defense Mechanism
Why encryption matters
The development of mempool encryption, which may mitigate the issues caused by MEV, has begun to show promise. By hiding transaction details prior to execution, pending transactions cannot be observed and front-run by malicious actors.
Threshold encryption designs have begun to become the preferred design for several reasons:
- Control of keys in a decentralized manner.
- Secure delaying of decryption.
- Compatibility with validator networks.
Different Models For Threshold Encrypted Mempools
There have been many unsuccessful attempts to create 'Encrypted Mempools' using an 'Epoch based design'. Shutter has taken the lead by creating a revolutionary model that is a combination of both technologies.
How It Works
1. Transactions will be encrypted for a certain time period while they are in the 'Epoch'.
2. After the 'Epoch' is over, validators will together share their keys to decrypt the transactions.
3. As the transactions are decrypted, there will be fewer opportunities for 'Miner Extractable Value' (MEV) because they were not able to see the transactions beforehand.
The 'Epoch' method of encrypting transactions has proven that encrypted transactions can be implemented in a 'Production environment', but it also has added delays and overhead related to validating and communicating.
Batched threshold encryption innovation
Batched Threshold Encryption is a new technique that improves efficiency through
- Multiple Decryptions of transactions with one key
- Decreasing validator communications costs
- Increasing the volume of transactions per second in use cases in the real world
By utilizing this batching approach, we have made tremendous progress towards developing scalable encrypted mempools that can operate at scale on the network without degrading the performance of those systems.
Visual Comparison of Encryption Models
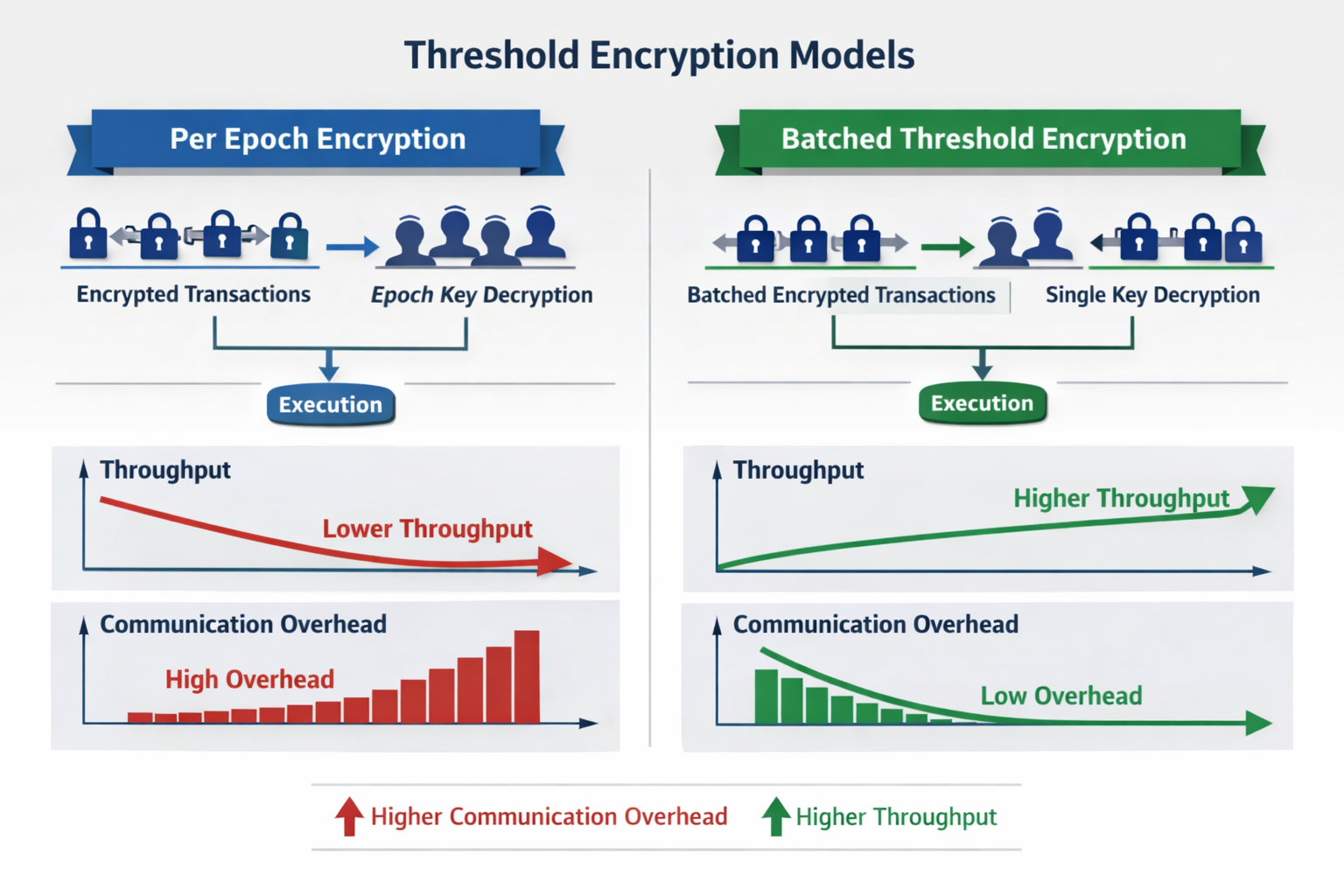
Image Source: Author
The Future of MEV Mitigation
MEV will still exist with just the use of "encrypted mempools," but they represent a significant change from an after-the-fact basis to one of a proactive prevention approach.
Ongoing research indicates that the ultimate long-term solution will be some combination of the following mechanisms:
Threshold encryption
Fair transaction ordering
Proposer/builder separation
Enhanced validator incentives
These mechanisms, when used together, would greatly reduce the potential for intentional extraction while still achieving the degree of transparency and decentralization that are essential to blockchains.
Conclusion
MEV attacks, or malicious miners extracting value by using the network to create, approve and broadcast their transactions first, are currently a serious ongoing threat to traders and are costing millions of dollars on a monthly basis to unsuspecting individuals . Since this is a developing ecosystem, significant progress has occurred with new threshold encrypted mempools that further advance the framework of defending users. Early experiments have already demonstrated the validity of the concept. With the introduction of new batched encryption solutions, we are now able to achieve a more secure and scalable environment for execution trades with MEV resistance.
The evolution of this technology is going to shift from speed and cost based developments to more equitable transactions through new transaction layer features.


